Network Traffic Analysis Protocols
Network Monitoring Solutions: Understanding Traffic Analysis Protocols
In today's complex digital landscape, effective network management depends heavily on robust traffic analysis and data packet examination. Organizations rely on comprehensive monitoring systems to maintain network integrity, optimize performance, and identify potential security vulnerabilities before they escalate into critical issues.
Examining network traffic provides administrators with crucial insights into data movement patterns, resource utilization, and potential bottlenecks. This visibility allows for proactive management and timely intervention when anomalies appear in the system.
The granular analysis of data packets reveals essential information about communication endpoints, protocols in use, and application behaviors. This detailed inspection capability serves as the foundation for identifying unauthorized access attempts, detecting unusual traffic patterns, and preventing potential security breaches.
Among the various technologies available for network monitoring, two protocols stand out for their widespread implementation: Cisco's proprietary NetFlow and the industry-standard sFlow. These solutions offer different approaches to traffic analysis while serving the common goal of network visibility.
Cisco developed NetFlow as an integrated monitoring solution for their network equipment. This protocol excels at identifying and grouping related packets into meaningful flows, providing context-rich information about network communications. The flow-based approach allows administrators to track communication patterns between specific endpoints and understand the nature of their interactions.
By contrast, sFlow adopts a more universal approach to network monitoring. This protocol samples network packets and provides broader compatibility across multi-vendor environments. Its scalable architecture makes it particularly suitable for monitoring high-speed networks without introducing significant performance overhead.
When implementing a network monitoring strategy, organizations must consider their specific infrastructure requirements, existing equipment capabilities, and monitoring objectives. While NetFlow delivers comprehensive flow data ideal for detailed analysis and troubleshooting, sFlow's sampling approach offers excellent scalability for large-scale deployments.
Regardless of the chosen protocol, effective traffic analysis empowers network administrators to maintain optimal performance, ensure security compliance, and quickly respond to emerging issues before they impact end-users or business operations.
NetFlow operates through a straightforward cycle involving the collection, summarization, organization, and interpretation of flow data. Its architecture comprises several essential components that facilitate this process. First, the flow exporter consolidates individual packets into structured flows and transmits these flow records to designated collectors. These collectors, which can be hardware or software solutions, are tasked with receiving, storing, and initially processing the incoming flow data, often utilizing a cache or database to manage the information efficiently.
At the core of analysis are flow analyzers—specialized tools that scrutinize the stored flow records to uncover detailed insights into network activity. When network devices such as routers that support NetFlow receive data packets, they analyze each packet for specific attributes or traffic statistics across all interfaces where NetFlow is enabled. These attributes are then compiled into flow records and sent to collectors for storage and further examination. Typically, routers export flow records upon completion of each flow, employing sampling techniques to mitigate the volume of data transmitted across the network. It’s important to note that flow records are metadata summaries rather than the actual data content of flows.
NetFlow offers invaluable visibility into network traffic patterns, empowering network administrators and network operations centers (NOCs) to monitor resource utilization, identify peak activity periods such as web browsing during working hours, and pinpoint access patterns for applications. This intelligence supports capacity planning and optimization efforts. Moreover, security teams leverage NetFlow data to detect anomalies, unusual traffic spikes, or suspicious behaviors indicative of security threats like data exfiltration or spam operations. By revealing resource consumption hotspots, NetFlow contributes to proactive security management.
Despite its strengths, NetFlow has certain limitations that users should consider. The performance impact on network devices can be significant, as processing flow data consumes resources and may degrade device performance. Additionally, Cisco’s NetFlow implementations typically restrict flow export to two collectors, which can limit comprehensive network visibility if more extensive data collection is required. Another challenge is the latency inherent in NetFlow data collection; there can be delays of up to five minutes between traffic occurrence and visibility, which can hinder real-time decision-making in high-availability environments.
In contrast, sFlow, developed by InMon Corporation, employs a sampling-based approach to traffic monitoring. Its core principle involves capturing random samples of packets or interface statistics at specified intervals, rather than recording every flow. The "s" in sFlow signifies "sampled," highlighting its reliance on probabilistic data collection. This strategy allows sFlow to scale effectively in high-speed networks, providing comprehensive visibility without overburdening network devices.
sFlow’s design facilitates detailed insights into network usage, routing behaviors, and traffic patterns across complex, high-speed networks. It is supported by numerous vendors including IBM, HP, Cisco, Dell, Alcatel-Lucent, and Aruba, among others. By leveraging statistical sampling, sFlow enables network managers to maintain system performance while still acquiring rich monitoring data, making it an ideal solution for environments where scalability and minimal impact are critical.
Network Monitoring Approaches
NetFlow vs sFlow: Understanding Network Monitoring Approaches
Network monitoring is essential for maintaining optimal performance and security. Among various monitoring protocols, sFlow stands out as a sampling-based approach that balances visibility with resource efficiency.
The sFlow Architecture
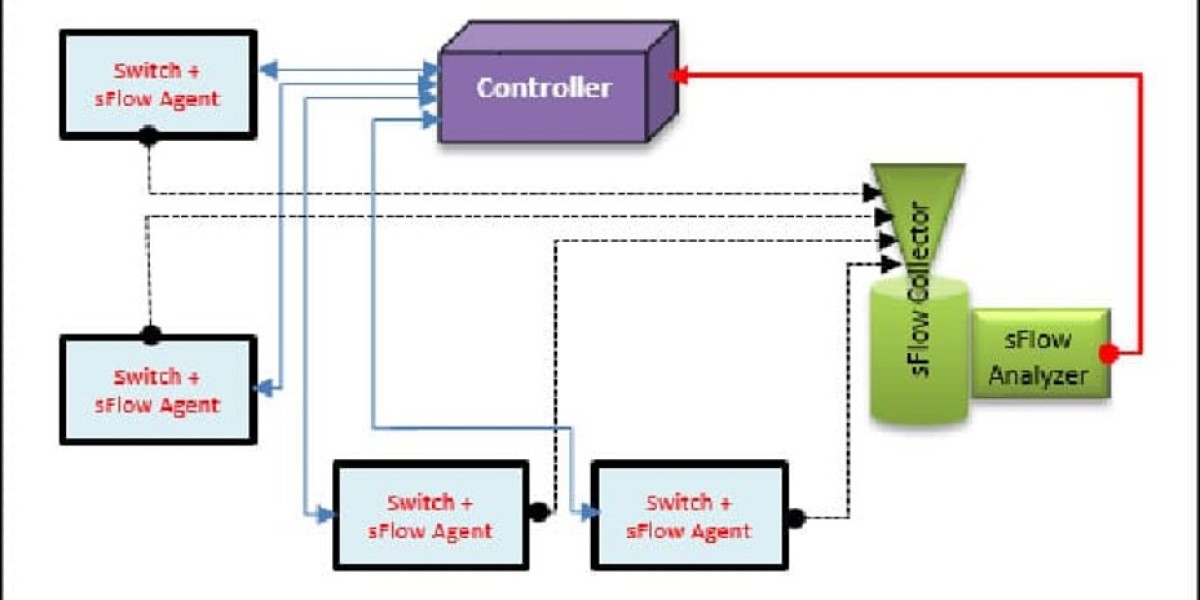
sFlow operates through a distributed monitoring system comprised of two primary components:
- sFlow Agents: Embedded within network infrastructure devices (routers, switches)
- sFlow Collectors: Central servers that analyze the sampled data
This architecture creates a lightweight monitoring framework where agents collect random packet samples and periodic counter information, then forward these to collectors for analysis.
How sFlow Sampling Works
The sampling mechanism is fundamental to sFlow's operation. Rather than capturing every packet, sFlow randomly selects a subset based on a configurable sampling rate (e.g., 1 in 1000 packets). Additionally, interface counters are sampled at regular time intervals.
The sampled data is immediately forwarded to collectors without local caching, which:
- Minimizes device resource consumption
- Enables deployment on high-speed networks
- Reduces overall monitoring overhead
Benefits of sFlow Implementation
Organizations implementing sFlow gain several advantages:
- Identification of traffic anomalies and potential security threats
- Visibility into network congestion points
- Ability to associate traffic patterns with specific applications or users
- Insights for route optimization and performance improvement
- Establishment of baseline network behavior for anomaly detection
Considerations and Limitations
Before implementing sFlow, organizations should consider:
- Device compatibility requirements across the network infrastructure
- The statistical nature of sampling versus complete packet capture
- Sampling rate configuration to balance accuracy with performance
- Potential visibility gaps compared to full packet inspection protocols
For networks requiring absolute precision or comprehensive security monitoring, the sampling approach may present challenges. However, for many environments, sFlow offers an effective balance between visibility and operational efficiency.
Choosing Between sFlow and NetFlow
When selecting a flow monitoring protocol for your network, understanding the key differences and considerations is essential.
sFlow is generally designed to impose minimal load on network and computing resources, making it an ideal choice for small to medium-sized environments with less powerful devices. It offers a lightweight approach, enabling continuous monitoring without significant impact on network performance. In contrast, NetFlow tends to gather more detailed data, providing comprehensive visibility into network traffic. However, this increased detail can come at the cost of higher latency and greater resource consumption, which might not be suitable for all network sizes.
The decision between sFlow and NetFlow often hinges on your organization's specific needs. If you require a broad, real-time overview with low overhead, sFlow may be preferable. Conversely, if in-depth analysis and detailed traffic insights are critical, and your infrastructure can handle the additional load, NetFlow could be more appropriate.
Compatibility also plays a crucial role. Many network devices from various vendors support one or both protocols. If your equipment supports only one, choosing that protocol simplifies deployment. If both are supported, leveraging both can provide a more comprehensive perspective, combining the lightweight efficiency of sFlow with the detailed insights of NetFlow.
Ultimately, your choice should align with your network’s scale, device capabilities, performance requirements, and the level of visibility you need to maintain optimal operation.
What is a Netflix VPN and How to Get One
A Netflix VPN is a tool that enables users to bypass geographical restrictions on Netflix content by connecting to servers in various countries. It is used to access a broader range of shows and movies that may not be available in the user's location. With a Netflix VPN, viewers can enjoy an expanded entertainment library regardless of their physical location.
Why Choose SafeShell as Your Netflix VPN?
If you're seeking reliable access to region-restricted Netflix libraries, you may want to consider the SafeShell VPN as your solution. This specialized service excels at delivering Netflix unblocked, overcoming geographical barriers to unlock a vast world of entertainment content that would otherwise be unavailable in your location. Its capabilities ensure you can enjoy shows and movies exclusive to other countries effortlessly.
SafeShell VPN provides exceptional advantages for streaming, starting with its high-speed servers specifically optimized for Netflix unblocked content, guaranteeing buffer-free, high-definition playback. You can seamlessly stream your favorite series and films without frustrating interruptions. Furthermore, SafeShell allows simultaneous connections on up to five different devices, supporting platforms like Windows, macOS, iOS, Android, and various smart TVs, meaning the whole household can enjoy different region libraries at once. Its unique App Mode takes this further, enabling access to multiple international Netflix libraries concurrently for unparalleled viewing freedom.
Beyond unlocking global content, SafeShell VPN prioritizes your security and offers flexibility. It employs advanced encryption and proprietary security protocols to shield your online activities and personal data during streaming sessions. Combined with its consistently lightning-fast connection speeds and unlimited bandwidth, you experience top-tier performance. To explore these powerful features risk-free, SafeShell VPN provides a flexible free trial plan, letting you test its Netflix unblocked capabilities, multi-device support, and robust security before committing.
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
To use NetFlix VPN on SafeShell VPN, start by subscribing to SafeShell Netflix VPN through their official website at https://www.safeshellvpn.com/ by selecting a suitable plan and clicking the "Subscribe Now" button. Next, download and install the SafeShell VPN app compatible with your device, whether it’s Windows, macOS, iOS, or Android. Once installed, launch the SafeShell VPN app and log in to your account. To optimize your streaming experience on Netflix, select the APP mode within the app. Then, browse the list of available servers and choose one located in the region whose Netflix content you'd like to access, such as the US, UK, or Canada. Click on "Connect" to establish a secure connection to your chosen server. Finally, open the Netflix app or visit the Netflix website, log into your account, and enjoy streaming content from the region you selected with your SafeShell Netflix VPN.